Elevating Our Security and Cybersecurity Protocols
Equitrans recognizes the critical importance of safeguarding our physical infrastructure assets and securing our informational resources and intellectual property. Today, more than ever, there are growing concerns related to the ability of an organization to protect its physical assets, as well as its critical technology assets, requiring companies to display incredible resilience in an ever-changing world.
As outlined in the Company’s Security Guidelines, Equitrans is committed to providing a safe and secure environment for all employees, customers, suppliers, vendors, and guests. These guidelines, available for employee access and reference on Equitrans’ intranet, are intended to create a consistent approach to protect people, assets, and information while mitigating risks to Equitrans. The Company’s guidelines are not intended to supersede government statutes or regulations and are updated as needed to support the needs of our business and operations.
Our Approach to Physical Security
From both a safety and business continuity perspective, it is crucial that we utilize stringent security measures for our pipeline assets, compressor facilities, and project sites. Trespassing and vandalism by those opposed to the fossil fuel industry can damage or destroy assets; create safety risks and hazards for our employees, contractors, and communities; and impact our ability to deliver natural gas to our customers. The disruption of natural gas delivery for our customers can impact consumers, businesses, and manufacturing facilities.
Equitrans works closely with the U.S. Transportation Security Administration (TSA) to ensure our enterprise abides by all federal security regulations, and we continually optimize our security strategies and plans. Our Security Team implements a wide range of security measures including:
- Site Support: In the event of an emergency or physical security threat, our security team supports site work by providing employees field encampment equipment, such as shelter, food, water, and portable bathroom facilities.
- Mobile Surveillance: Our security team oversees potential security threats by monitoring mobile surveillance, including security cameras and drones. When our security team detects a threat, team members evaluate potential risks, or the extent of the incident, and deploys proper mitigation strategies.
- Physical Security: We use barriers and other physical security measures, such as locks, fencing, and barbed wire, to prevent facility tampering and trespassing.
- Security Personnel: The security team deploys static and roving security guards to provide physical security at our critical sites and in areas where they detect security threats. The security team also works with local law enforcement to protect sites and respond to threats.
- Drone Support: Our security team utilizes trained and licensed drone pilots to conduct aerial security surveillance. Our drone teams support additional operational needs, such as land surveys and data gathering.
Security Training
Equitrans contracts all security guards from a third-party security vendor. Our security guards receive safety and security training from their employers, and we also provide all of our security team members and third-party security personnel with formal security training and information on Equitrans-specific security standards. Additionally, in early 2023, Equitrans launched mandatory training sessions for all employees on the topic of environmental justice and human rights. These sessions are available to Equitrans’ third-party security vendors and contractors, as requested.
Prior to starting work at any site, security guards are required to attend a comprehensive security training session to identify and be familiar with any site-specific hazards or risks, with the type of training dependent upon the specified operating location and the conditions on the ground. Our training program includes the following concepts:
- Pipeline Security: How to protect our pipelines from trespassers, physical threats, and disruptions
- Law Enforcement: How and when to involve law enforcement agencies
- Crisis Events: How to respond to a crisis or emergency on or near a project site
- Field Sabotage: How to detect sabotage efforts that could affect pipeline integrity
100% of our security personnel receive formal training on Equitrans’ safety and security practices.
We also train guards on the legal requirements and technical use of body cameras, as well as techniques for effective and safe protest management. Many of our guards also have specialized executive protection training and routinely receive updated training on trespassing and specific instructions for protecting Company vehicles stored in Company parking lots. In early 2022, we implemented Standard Operating Procedures to deploy drone aircraft for safety overwatch in contentious areas. This new feature to our security program is expected to result in cost savings and enhance our ability to rapidly collect information.
At our operational facilities, our security guards increase overall safety and minimize the risk of serious incidents by providing direct oversight and immediate response to potential incidents involving opponents. In the event of a dangerous incident, Equitrans’ security team works to safely evacuate work crews and initiates assistance from law enforcement, if needed.
Asset and Operations Security
The security of our pipelines and facilities is integral to national and economic security and the success of our operations. Ensuring we are safeguarding our assets also reduces risks of environmental incidents and potential safety hazards. We protect our assets with fences, building locks, electronic monitoring, and 24/7 surveillance at many of our sites, and for pipelines and compressor stations that are in operation, Equitrans continuously gathers information regarding their security. In addition, security guards are routinely scheduled to be on location at various compressor station facilities and project sites, including along the Mountain Valley Pipeline (MVP) project route. Our operations team determines the criticality of a site by analyzing the level of risk for disruption and the potential impacts on our local communities, on-site employees, contractors, equipment, and capacity throughput.
At construction sites, we deploy various levels of security, depending on their criticality and vulnerability. For critical sites, we secure pipe storage yards and worksites with 24/7 security guards or advanced analytic camera systems. At sites where an increased threat may exist, we employ both security guards and camera systems simultaneously.
The majority of our pipeline construction projects require us to hire guards during non-work hours and Equitrans’ Security Team oversees the security at all construction sites. If theft, vandalism, or other threats are encountered, a combination of roving and static guards along with varying levels of camera coverage will be employed to secure the site. For projects that encounter hostile persons or opposition during construction, we assign security teams to protect workers during the day and static guards to protect equipment during non-work hours. As an example, the MVP project has contracted nearly 100 roving and/or static guards to protect workers, equipment, materials, and construction sites. If we encounter a hostile person or group during construction, we contact the appropriate law enforcement groups and implement security and static guards to ensure our workers and equipment are safe.
Security guards also protect compressor stations and various other sites based upon criticality and vulnerability. Additionally, barbed-wire fencing and access controls, along with high-resolution analytical camera systems are used when deemed necessary. Other sites such as interconnections and metering stations incorporate fencing, cameras, or both, depending on the perceived threat to the specific location.
Office Security
Equitrans uses physical security measures in our offices to protect our employees, information technology infrastructure, and other assets, and security guards are stationed 24 hours/day, seven days a week at our headquarters office in Canonsburg, PA. We use gates, trespassing signs, and motion-activated cameras to deter unauthorized persons from entering our offices. We implemented an anti-tailgating system at the entrances of our headquarters office that signals an alarm when two people walk into the office together when using only a single employee badge. The headquarters office security personnel are CPR and AED certified and are trained to assist emergency medical service responders by quickly escorting them through building security. We continue to evaluate emerging risks and explore new ways to ensure the safety and security of all our offices.
Evaluating Our Physical Security
With oversight by the HSSE Committee of the Board, Equitrans’ approach to physical security is intended to reduce the risk of both major and minor incidents. As part of our physical security program, our security team works diligently to ensure all aspects of our enterprise are safe, including Equitrans' employees and assets, contractors, and local communities. We track regional, national, and global protests utilizing the Welund database.
To promote respect for human rights, all of our security guards are directed to “observe and report” and are expected to follow strict orders to have no physical contact whatsoever with community members or the public-at-large, including opponents. When confronted with physical opposition, our guards are trained to assist staff with safe evacuations, notify appropriate law enforcement authorities, and document the incident in detail as a witness. There are, however, select situations or circumstances where it may be necessary to have a presence of armed guards with arrest powers, although that is not standard protocol at all locations.
Our operations team determines the criticality of a site by analyzing the level of risk for disruption and the potential impacts on our local communities, on-site employees, contractors, equipment, and capacity throughput.
In late 2021, we partnered with the U.S. Transportation Security Administration (TSA) to comprehensively review Equitrans’ physical security program and began to voluntarily standardize our security measures to better align with emerging federal security expectations and regulations. We have since completed our 18-month follow-up with the TSA and have implemented each of the suggestions from their initial review. Additionally, for the safety and security of our employees, Equitrans implemented an overseas travel process that assesses U.S. State Department information and provides travel safety guidance for specific destinations. Equitrans is always looking for new ways to improve our security and protect our customers and communities, including consistent monitoring of our systems for vulnerabilities and efforts to mitigate any risks.
Our Approach to Cybersecurity
Cybersecurity is at the core of our technology strategy, the activities of which are managed by our Chief Information Officer and reviewed and monitored by our Executive Management, with oversight from our Board of Directors. The Company’s cybersecurity program forms the foundation of that strategy and is managed by our Senior Director of Cybersecurity and Network Operations. Together, our cybersecurity leadership team has more than 30 years of experience and multiple industry-recognized cybersecurity certifications.
We understand the importance of cybersecurity as it relates to our role in providing critical infrastructure for our nation’s economy and national security, and our cybersecurity program aims to protect and secure our technology-based informational assets, as well as our operational assets to meet customer demands. We do this by leveraging skills across departments, applying sophisticated cybersecurity practices, and maintaining accountability to leadership.
Informed by our enterprise risk management program, we utilize risk-based analysis in decision-making to determine actions and priorities for our cybersecurity program.
Given the importance of Equitrans’ cybersecurity program, in April 2022, our Board elected to exercise direct oversight of cybersecurity matters, rather than acting through the HSSE and Audit Committees. The Board receives management reports on cybersecurity matters, as needed and no less than quarterly throughout the year, which include items such as cybersecurity updates, cybersecurity operational results, and audit findings. In addition, the Board receives and reviews the results of the Company’s risk and capabilities assessment on an annual basis.
Our cybersecurity program is designed to:
- Leverage technology to securely and efficiently achieve business objectives
- Establish situational awareness of evolving technology-related threats and vulnerabilities
- Proactively detect and respond to cyber-attacks, minimizing adverse impacts to business operations
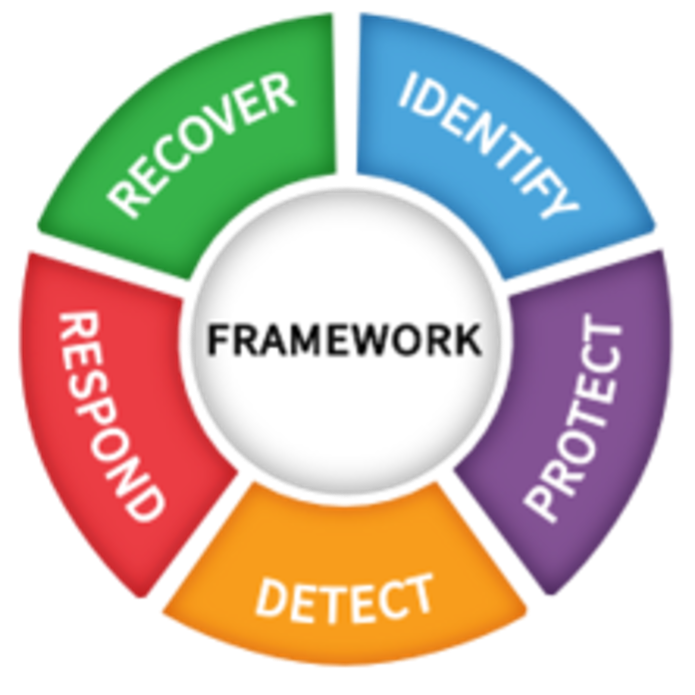
As a core design principle, Equitrans’ cybersecurity philosophy incorporates security requirements into our architecture, processes, and solutions. To affirm capabilities and identify opportunities, we developed a cybersecurity assessment program that is comprised of annual activities. To validate the effectiveness of our approach, we measure our capabilities and practices against the National Institute of Standards and Technology (NIST) Cybersecurity Framework, relevant industry standards, and government regulations. In addition, we routinely engage independent third-party security firms to exercise and assess our cybersecurity capabilities.
Cybersecurity Program
Equitrans’ cybersecurity program has evolved through contributions from our technology team’s talent and experience, our security and legal partners’ knowledge and guidance, independent audit reviews and assessments, regulatory compliance inspections and recommendations, and information sharing with industry groups and government agencies. Similar to other companies in the natural gas industry, we recognize that no cybersecurity program is invulnerable, and we have identified, and expect to continue to identify, cyberattacks and events on our systems. In doing so, we have taken steps to reduce the probability of a future event and, should a future event occur, to reduce the potential impact to our business and operations.
Our cybersecurity program includes architecture, processes, and automation. Equitrans practices proper cyber hygiene through rigorous identity and access management, vulnerability and patch management, and asset management programs. These programs are designed to reduce the attack surface for adversaries and allow us to proactively manage our user accounts, systems, and devices. We also segment our informational and operational technologies, as appropriate, and leverage network micro-segmentation to further protect our critical systems and assets. This practice, in line with zero-trust security concepts, restricts lateral movement within our network and allows only necessary and required access.
Equitrans’ cybersecurity approach extends to include vendors managed through our supply chain. We established a formal set of technology requirements for suppliers and contractors, by which third parties acting as contractors or suppliers for Equitrans must abide by uniform use and access requirements when utilizing the Company's technology resources. These requirements, which are included in our Supplier Code of Conduct and provided during the supplier onboarding process, support the integrity and security of Equitrans’ resources and related information, including the appropriate handling of Personally Identifiable Information (PII). In addition, contractors and consultants that have access to Company data, devices, or services are required to complete cybersecurity training prior to receiving access. We believe our structured approach to technology management with third-party vendors demonstrates our commitment to protecting the Company’s critical data.
Capabilities
As essential components of our technology strategy, we appreciate that cloud and internet services continue to transform the technology landscape. We believe embracing cloud and internet technologies has improved our resilience and demonstrated performance improvements, while also ensuring enhanced security controls and visibility. To provide consistent and holistic security visibility in a cloud-computing environment, we established a virtual perimeter around our data, applications, and services by integrating our cloud-hosted services with our security operations center. To enable our cloud approach, we believe Equitrans has built a modern high-performance network to provide secure and resilient connectivity between Internet and cloud services and our field locations.
Operationally, we continuously monitor for cyber intrusions, augmenting our internal resources and capabilities with that of third-party service providers. Multiple security technologies are employed to protect our systems, applications, and data, including next generation firewalls, strong multi-factor authentication and access controls, and endpoint detection and response solutions. Collectively, we believe these technologies protect, secure, and segment Equitrans information while traversing home and public networks.
To support our remote workforce, Equitrans utilizes a scalable, cloud-native architecture to provide secure access service for mobile users from anywhere. We also employ a network monitoring and detection solution designed to baseline network activity and identify anomalies in our network.
Detection and Response
Beyond our data privacy policies, additional access restrictions and monitoring are in place for data related to our customers’ and landowners’ PII, and similar protections are in place for commercially sensitive data and systems. Additional protections are provided via active alerts and monitoring for data movements and with electronically enforced policies such as prohibiting USB storage devices.
In addition to active threat prevention and detection, we believe our cybersecurity program includes robust containment, response, and recovery capabilities. Our fault-tolerant, highly available architecture is an important part of our continuity and containment through network segmentation and micro-segmentation designs; however, Equitrans does not solely rely on architecture to ensure continuity and containment. Automated account disabling, automated device quarantining, and network segment-isolation scripts are examples of response technologies and processes that enhance containment during an incident. Response capabilities also include cyber kill chain runbooks to thwart bad actors or malicious code from traversing our environment.
An important part of our recovery capabilities is our data backup program. We believe we adhere to a robust Enterprise Data Backup Policy, which includes, among other activities, offsite backups, intra-day recovery points, and routine restoration of critical data. We are also able to quickly recover virtualized servers and network appliances through infrastructure-as-code and data replication to multiple operating regions. We routinely exercise our recovery capabilities as part of upgrade and patch testing.
Our Crisis Management Plan includes specific response activities for cybersecurity incidents. We conduct routine cyber incident drills that include cross-functional participation by our executives, business stakeholders, and legal and security partners. Through these exercises we evaluate the effectiveness of our outlined response plans and procedures.
Education and Training
Our technology governance is documented through written policies, standards, guidelines, and standard operating procedures, and we implement electronic enforcement as a monitoring tool to ensure compliance and assist in preventing undesired behaviors. We prioritize training and cybersecurity awareness for our employees and extend this training to include our service providers and partners. Quarterly cybersecurity training is required for all employees. This training and awareness content covers topics such as knowledge of cybersecurity policy, understanding of cyber threats, and incorporation of leading practices into their daily IT- and cyber-related activities. Equitrans employees and partners with access to our operational technology (OT) network are required to participate in additional training specific to OT interactions.
Evaluating Our Cybersecurity
Due to the critical nature of our business to the U.S. economy and national energy security, cybersecurity is a top tier enterprise risk. With this designation, cybersecurity mitigation activities are incorporated into our daily operations and business strategy, as well as our financial planning and capital allocation processes related to the annual budget approved by our Board.
Equitrans’ cybersecurity assessment program is built on the concept of multiple security firms performing independent reviews to continuously assess our vulnerabilities and capabilities.
Our enterprise risk management program assesses operational, financial, and government and regulatory risks that threaten the achievement of the Company’s objectives. As part of this program, executive and senior leadership convene quarterly to re-assess risks, report to the Board annually on enterprise risks, track mitigation activities, and identify emerging risks. The program includes quarterly technology and cybersecurity risk assessments, the results of which we utilize to conduct risk-based decision making to determine actions and priorities for our cybersecurity program. The technology and cybersecurity risk assessment process includes an objective, risk-ranking process; documented mitigation activities; and action plans for those risks requiring additional mitigation. These activities consider safety implications, operational disruptions, and business and financial impacts.
Another critical component is our cybersecurity assessment program, which is built on the concept of multiple security firms performing independent reviews to continuously assess our vulnerabilities and capabilities. Additionally, Equitrans’ IT leadership routinely conducts risk quantification and assessment exercises to enhance the resiliency of our systems, ensure the effectiveness of our cybersecurity program, and minimize the risk of cybersecurity activity. We augment those reviews with self-assessments, purple team exercises, and incident response exercises to provide comprehensive feedback to our readiness. We believe this continuous improvement approach to cyber protection and response allows our program to remain flexible and dynamic, allowing us to adapt to ever-changing threats within the expanding cyber landscape.
Equitrans’ IT group actively works to comply with applicable TSA security directives and leading cybersecurity practices to protect Equitrans’ digital assets and operational capabilities. We continuously engage with relevant government agencies to report and share security information enabling us to benchmark our capabilities, establish appropriate program targets, and adapt to emerging cybersecurity issues.